Web Application Firewall (WAF) vs Next Generation Firewall (NGFW): What is the difference?
There are a number of issues that fuel the confusion surrounding NGFWs and WAFs. First, because both technologies are called firewalls, some people may think they are similar. And because NGFWs are an evolution of traditional network firewalls, the terms are sometimes used interchangeably. However, while both technologies serve to inspect and stop malicious intrusions, each offers a different layer of protection.
We can think of an NGFW as the entrance to a hotel and the WAF as the key to a hotel room.
Staying ahead of the next data breach or DDoS attack means staying alert and making real-time decisions when deploying network and application defences.
What is the difference between WAF and NGFW?
WAF (web application firewall)
A web application firewall (WAF) is a type of firewall that monitors, filters or blocks HTTP traffic to and from a web application. It differs from a normal firewall in that it can filter the content of specific web applications, whereas a network firewall protects traffic between servers. By inspecting HTTP traffic, a WAF protects web applications against attacks such as SQL injection, XSS and cross-site request forgery (CSRF).
It is usually aware of the user, the session and the application and knows the web applications behind it and the services they offer. The WAF can therefore be seen as an intermediary between the user and the application itself, which analyses all communications before they reach the application or the user. Traditional WAFs ensure that only permitted actions can be performed (depending on the security policy). For many organisations, WAFs are a reliable first line of defence for applications, especially to protect against the OWASP Top 10.
NGFW (next generation firewall)
It monitors traffic going out to the Internet (via websites, email accounts and SaaS). In short, it protects the user (versus the web application). The NGFW enforces user-based policies and adds context to security policies, in addition to other functions such as URL filtering, anti-virus/anti-malware, and potentially, its own intrusion prevention systems (IPS). While the WAF is typically a reverse proxy (used by servers), the NGFW is typically a forward proxy (used by clients as a browser).
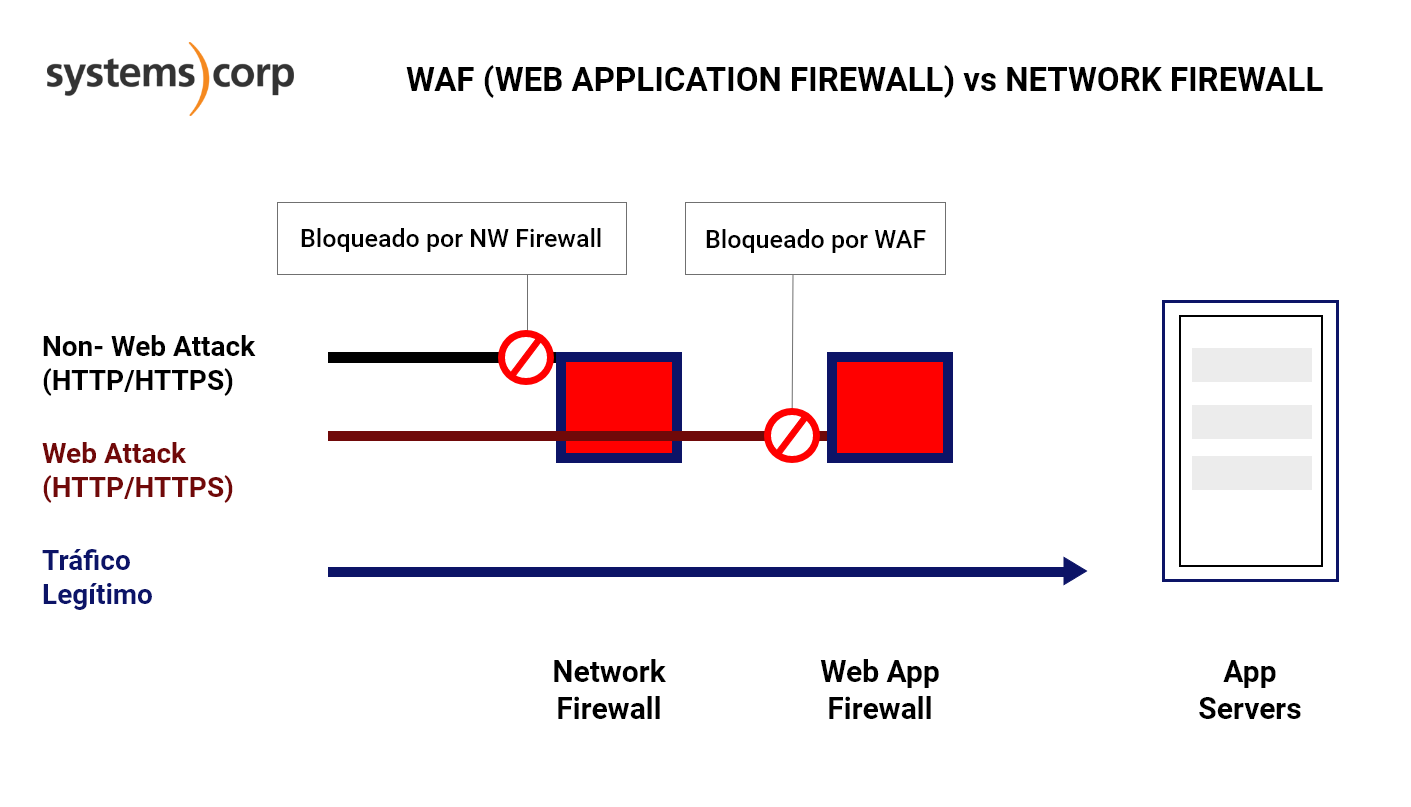
Traditional firewalls are divided into three functions:
Filter, inspect and allow or disallow. While NGFW firewalls offer a range of additional protection such as detection and prevention of malware and DDoS attacks, WAFs offer protection against web threats (such as phishing hack attempts).
WAF Vs Firewall:
Traditional network firewalls mitigate or prevent unauthorised access to private networks. Firewall policies define the traffic allowed on the network, and any other access attempts are blocked. Examples of network traffic that this helps prevent are unauthorised users and attacks from users or devices in less secure areas.
A WAF focuses specifically on application traffic. It protects HTTP and Hypertext Transfer Protocol Secure (HTTPS) traffic and applications in Internet-facing areas of the network. This protects enterprises against threats such as cross-site scripting (XSS) attacks, distributed denial of service (DDoS) attacks and SQL injection attacks.
Appliance-based WAF or cloud-based WAF.
Traditional on-premise WAF appliances have evolved to cloud-based services and broader feature sets.
The fundamental difference between a cloud WAF and an on-prem WAF is the way they are deployed. A cloud WAF is accessed via a web interface or mobile app and is provided as software as a service (SaaS); whereas an on-prem WAF runs in your data centre, or as a virtual machine within your Infrastructure-as-a-Service (IaaS) cloud presence, which, when outside the local area network, is accessed via LAN and VPN. There are pros and cons to both.
Cloud-based WAF deployments are typically faster than on-prem WAF options. On-premises WAF deployments can take up to several months depending on the size of the enterprise, the number of users, the various locations in which it should be deployed, and the unique customisations required. Cloud-based WAF deployments tend to be considerably faster, in part because they offer fewer opportunities for customisation.
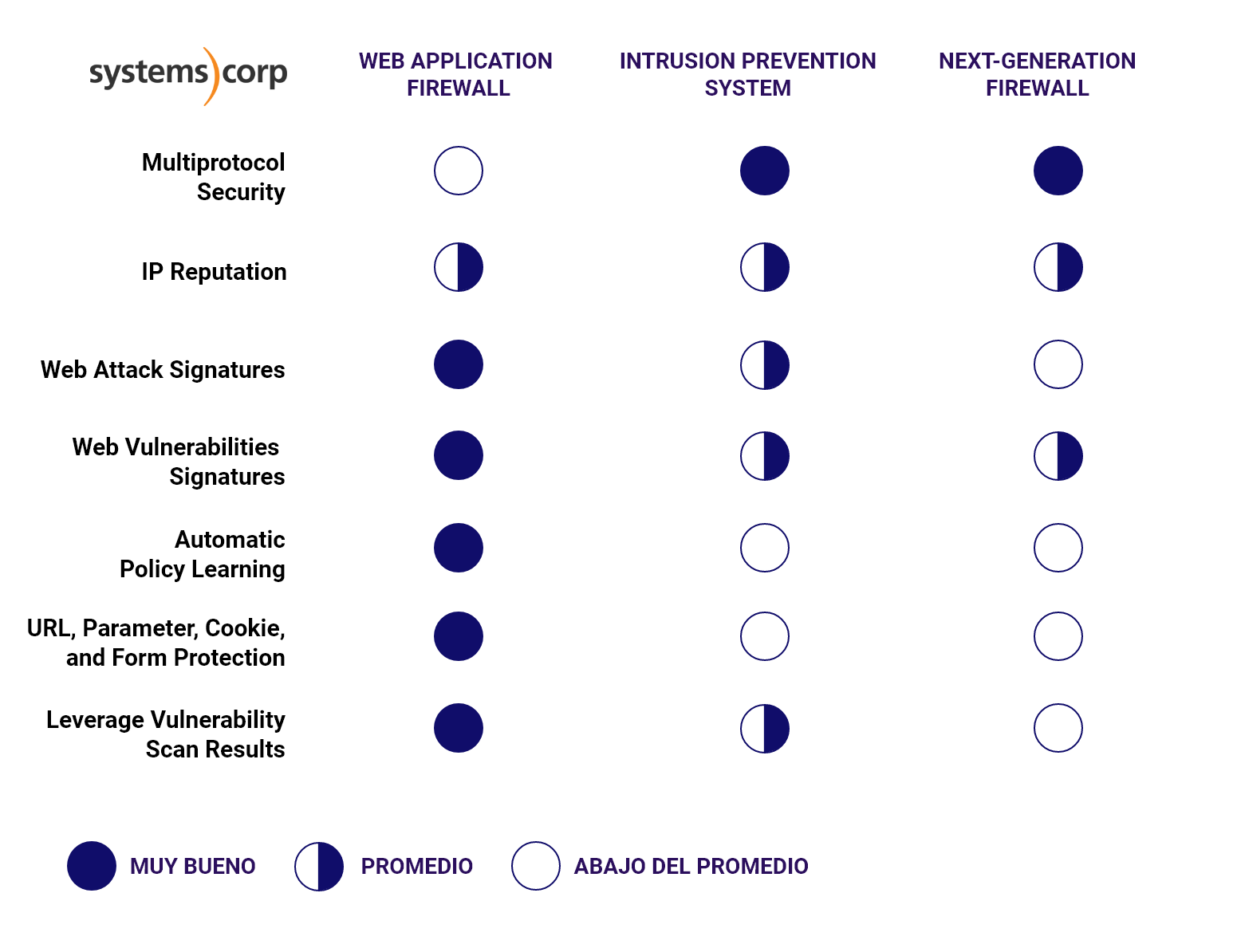
Both technologies are important
Given the various potential points of intrusion in both a network and a web application, in most cases it is important to employ both technologies. Both NGFWs and WAFs are considered network functions, but they interact with traffic at different points.
Web applications are increasingly the target of malicious attacks that exploit commonly known vulnerabilities. Cross-site scripting and SQL code injections are among the most common attacks.
Network firewalls are based on a set of basic rules that cover the network traffic; WAFs cover the application. The joint use of an NGFW and a WAF provides broader coverage. It is also important to set these rules so that they are automatically updated to include protection against new vulnerabilities without the need for additional configuration.
A network firewall can help stop an attack at the network edge by blocking incoming malicious traffic, which can benefit an application to some extent. The WAF will stop specific layer 7 attacks against the application, whether it is an attempt to exploit vulnerable software libraries or code-level vulnerabilities, such as deserialisation or injection attacks, or a DDoS attack targeting the application's computing resources.
You can contact our security specialists without obligation so that we can analyse how your organisation is protecting itself in the different layers of corporate security.
If you're not sure how to get started, leave your details and we'll contact you as soon as possible.
We can accompany you in your end-to-end projects. Let's work together.

